If you’ve come here from a link on twitter — you’d see that the address bar still says login.astro.com.my, but the site is rendering this page from my blog. If not, click this link to see what I mean. You’ll get something like this:
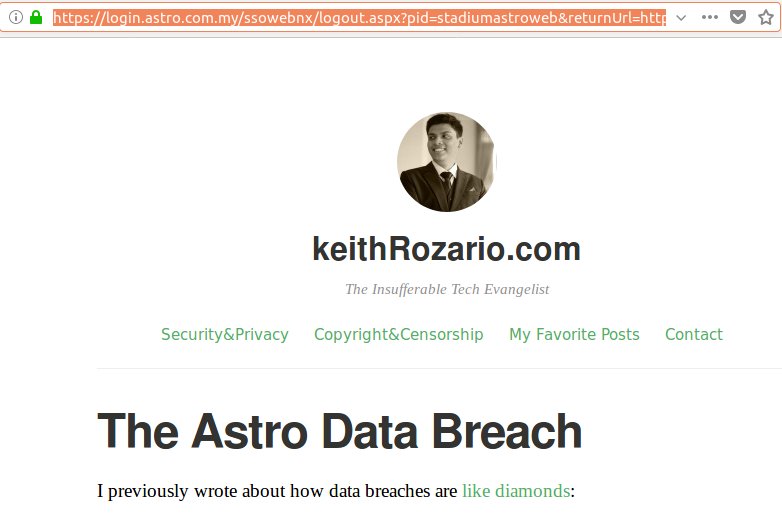 Somehow I’ve managed to serve content from my site on an astro domain. Rest assured, I haven’t ‘hacked’ astro servers and uploaded my page, but I’ve performed an equally sinister attack called open redirect.
Somehow I’ve managed to serve content from my site on an astro domain. Rest assured, I haven’t ‘hacked’ astro servers and uploaded my page, but I’ve performed an equally sinister attack called open redirect.
While browsing online for some more info on the astro breach, I found this blogpost from Amirul Amir, detailing the open redirect vulnerability on astro’s website. The post is dated Nov 2016, yet the vulnerability still works — and even though Amirul laments that he informed Astro, they seem to have taken no action in more than a year.
You might be wondering what good is an open redirect vulnerability?
Well, an attacker might send you a phishing email, pretending to be astro asking for you update to update your info on their site, and they’ve even included a conveniently placed a link for you to click. The link looks legitimate (it has login.astro.com.my in it), so you click it to a find a legitimate looking site, with valid certificates to boot — so you enter your username and password.
But the site isn’t legitimate, it’s an attackers page (that looks exactly like Astro’s) rendered over the original website, leveraging the vulnerability (and some added javascript) — and now you’ve just given your username and password away.
The frustrating thing with open redirect, is that all the techniques we educate people to use for detecting phishing sites, don’t work in this case — because this is the ‘real’ site, that’s been compromised by open redirect.It has the correct domain, it even has the right certificates, the only way you’d know is if actually look into the embedded javascript, but 99% of folks never do that.
So for a company like Astro to be sitting on this vulnerability for more than a year is not acceptable.
Just more bad news for their already shitty response to the original data breach.
Shout out to Amirul who blogs over at kaizen1996.wordpress.com,although it looks like he stopped blogging in 2016, pity because he had good content.