OK….I made a boo boo!
Actually my method of ‘hacking’ the Unifi modems has a ridiculously simple work-around. Unfortunately, when I published the findings I was absolutely convinced the workaround didn’t work–I was wrong 🙁
Details about how I was mis-lead are unimportant for now (although I will explain it later on), for now I think the simplest way to address and to make yourself more secure (though not 100% secure) is to disable remote management of the router. Don’t worry here’s a step-by-step guide on how to do it.
Step 1: Logon to your router
To logon to your router, fire up your web-browser (Chrome, Firefox, Safari–even Internet Explorer will do). In the address bar where you usually type www.google.com type http://192.168.0.1 or just click the link. Once there enter the username and password of the router. If you’re uncertain try any one of the following combinations:
Username: Management Password: TestingR2
Username : operator Password : h566UniFi
Username : operator Password : telekom
Username : operator Password : <your Unifi username in reverse order>
Otherwise refer to this post on how to find your router password. Click here, and look for option 3.
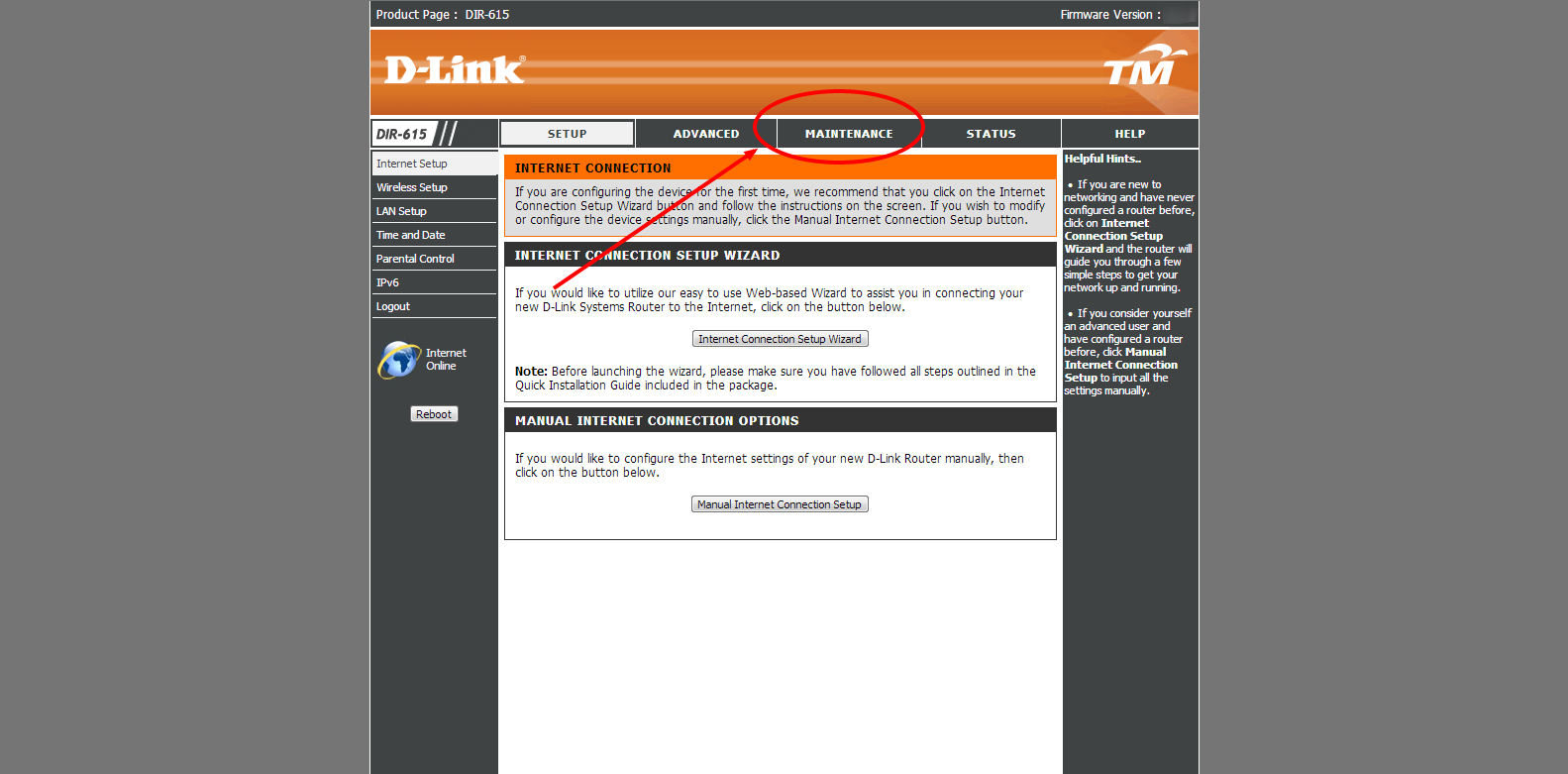
Step 2: Head on to the Maintenance Section
Once logged on, click on the Maintenance tab of the router.
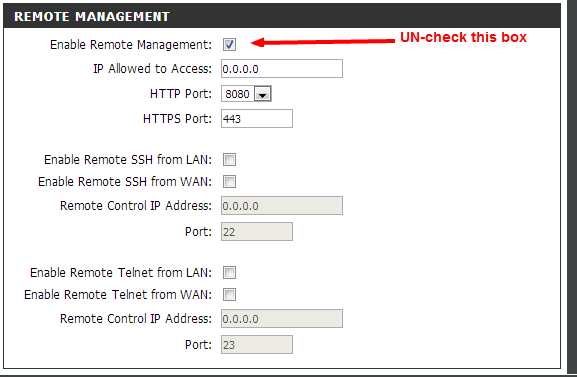
Step 3: Uncheck the box that says Enable Remote Management
Once you’ve entered the Maintenance tab, uncheck the “Enable Remote Management” check box. The image on top has the box check, you want to make it empty.
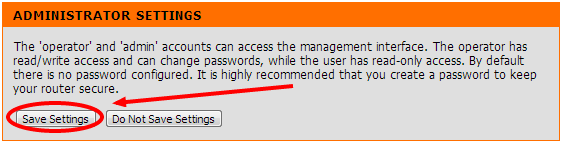
Step 4: Save those damn settings
Finally make sure you save those settings, otherwise all your hard effort would have been wasted. Once you’ve saved your settings, the router will either inform you of the setting change or it’ll take you back to the router login page (same as step 1)
Step 5: Reboot the router for good-luck
Finally for extra good luck, reboot your router, and check if the settings are still the same. Some funky stuff sometimes occur between reboots. Rebooting is easy, just switch off the power to the router for 10-15 seconds, then re-start it again.
That should do it. Easy wasn’t it.
How I was wrong
Aiyah–this was a bit of a boo boo lor, everyone makes mistakes mah 🙂
Firstly, what you’ve done in the 5 steps above, is disable anyone from outside your home network from accessing the router. That means the only way you’ll ever access your router config page is via your internal network and not from the internet. So your router IP won’t even show up in the Shodan results and even if it did, your router wouldn’t allow these external IPs from accessing it’s page.
Where I was wrong is that I thought this feature didn’t work on the Unifi router, and to be fair there are plenty of Dlink routers that have this flaw. It didn’t help that there were support forums that explicitly addressed this. Where I was wrong of course, is that when I tested this–I tested it from within my own network. From within my network, regardless of whether I used the internal or external IP, I could still access my router, I was under the impression that if I entered the external IP, it would only work if remote access was enabled–I was wrong. I should have tested this from an external network, and using my phone or even a web-proxy I would have easily realized that this fix works for my router (and possibly yours as well).
So if you want to be sure that your router is no longer allowing GUI access over the internet, head on over to Texas Proxy, and then type your external IP to see if you can view your router login page, you should get a curl error, and that would confirm you’re good to go.
Now of course, I was wrong, and I’m sorry if I caused you to panic, or worse yet go out and splurge on a new router. I’ve been wrong before, and this probably isn’t going to be the last time either–being wrong is part of the job, I try to avoid it, but sometimes it’s unavoidable. The only thing I can truly offer, is my apologies for being wrong–and I really am sorry. To show just how sorry I am, take a look at the picture below (can you really still be angry with me after seeing those sad eyes?)
Conclusion
Now, the final word though, is that while the fix will protect you, I’m not 100% sure why TM chose to NOT disable the remote login by default. From my quick check, most routers with the 7.17 firmware have this feature enabled and that’s a really bad thing.
Also, this isn’t 100% full-proof, the exploit still exist, and if someone manage to compromise your laptop, desktop or even IP Camera, they may have a back-door to your router, but making this one check (or un-check) makes you FAR more secure than before.

[…] To address the issue check out my post on how to prevent this on your Unifi router, click on my post here. […]
TM do not disable remote access for reasons. I noticed that firmware update only granted by superuser, not admin of router itself. 40% i guess who purchase internet know to access their router, the rest of it only common user. Maybe details can be refer in term & agreement. Big brother watching you:)
I really doubt TM perform firmware updates over the web. It’s not advisable under any circumstance.
The analogy is that you buy a house from a developer, and the developer grants you a warranty period of defects. However, do you give the developer a key to your house, so he can come in any time he pleases–or do you keep the key and tell the developer only to come around when you’re at home to supervise him.
In making their support processes easier, TM have also reduced the security of their users on the internet. Not a good choice.
Its as ipedo says, most of the consumers that subscribe to an isp do not know how to access the router page. Due to that reason, remote access is left on, as TM (Level 2 and above) will be able to check out your router page to check the settings. It is much more time/cost effective then sending a technician.
@kar2on:disqus
Feeling very frustrated after viewing your video “http://www.keithrozario.com/2014/01/hack-unifi-in-5-minutes.html”. This is old news. Like 30th May 2010 old. Old until the site dead liao (http://archive.is/6kT9D). People already complained/gave feedback to TM back then and if fell on deaf ears. Why? It is part and parcel TM’s troubleshooting workflow.
Hello there.. Can I keep my router secure if I change the Management password?
TQ 🙂
so far I’ve been unable to crack firmware version 7.19 and higher, but you never know. I would say NO!
[…] Just changing your Wi-Fi password is not enough, as I demonstrated when I logged onto some unsuspecting unifi subscribers without even accessing their WiFi. Be sure to disable remote access to your Router to ensure that no one can access your router from the internet as well. Follow the instructions here. […]
there is no maintenance section button, so i cannot unchecked my ‘remote managament’. pls help
Hey there,
Could I check what version router you’re using?
Keith
Hi , thanks for helping me, you are such a genius 🙂 would u mind to show me how to change my management passowrd? Thanks
TM do not disable remote access for reasons. I noticed that firmware update only granted by superuser, not admin of router itself. 40% i guess who purchase internet know to access their router, the rest of it only common user. Maybe details can be refer in term & agreement. Big brother watching you:)
I really doubt TM perform firmware updates over the web. It’s not advisable under any circumstance.
The analogy is that you buy a house from a developer, and the developer grants you a warranty period of defects. However, do you give the developer a key to your house, so he can come in any time he pleases–or do you keep the key and tell the developer only to come around when you’re at home to supervise him.
In making their support processes easier, TM have also reduced the security of their users on the internet. Not a good choice.
Its as ipedo says, most of the consumers that subscribe to an isp do not know how to access the router page. Due to that reason, remote access is left on, as TM (Level 2 and above) will be able to check out your router page to check the settings. It is much more time/cost effective then sending a technician.
@kar2on:disqus
Feeling very frustrated after viewing your video “http://www.keithrozario.com/2014/01/hack-unifi-in-5-minutes.html”. This is old news. Like 30th May 2010 old. Old until the site dead liao (http://archive.is/6kT9D). People already complained/gave feedback to TM back then and if fell on deaf ears. Why? It is part and parcel TM’s troubleshooting workflow.
Hello there.. Can I keep my router secure if I change the Management password?
TQ 🙂
so far I’ve been unable to crack firmware version 7.19 and higher, but you never know. I would say NO!
Hi , thanks for helping me, you are such a genius 🙂 would u mind to show me how to change my management passowrd? Thanks
there is no maintenance section button, so i cannot unchecked my ‘remote managament’. pls help
Hey there,
Could I check what version router you’re using?
Keith