Initially I wrote about PRISM and how a lot of people felt it was a tool to intercept communication in flight to companies like Google and Facebook, however slightly more details have emerged to debunk that claim.
However, it’s of paramount importance that we understand what people are saying. No one is denying that communications aren’t being intercepted on their way to Google, Facebook or Apple, instead what they are denying is that the capability to perform that interception and storage is under purview of another program called Upstream, and that analyst like Edward Snowden at the NSA were encouraged to use both PRISM and UPSTREAM.
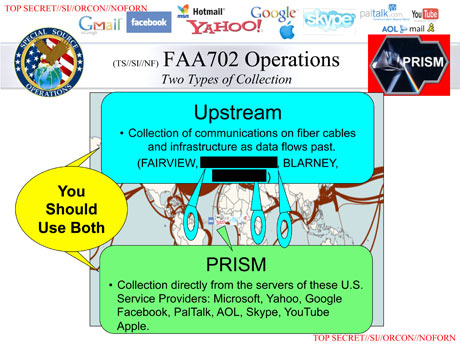
What the crudely drawn powerpoint on the left is trying to describe is the distinct-ness of the programs and how each program would complement (rather than replace) the other.
The release of this particular slide was done shortly after the initial news broke to, in the interests of aiding the debate over how Prism works.
The Guardian have intentionally redacted some of the program names from the slide, presumably in an effort to milk this story dry for all that it’s worth, but probably also to keep the momentum of the debate just in case people move on. However, in their own words the slide:
details different methods of data collection under the FISA Amendment Act of 2008 (which was renewed in December 2012). It clearly distinguishes Prism, which involves data collection from servers, as distinct from four different programs involving data collection from “fiber cables and infrastructure as data flows past”.
The of course points to separate approaches, one where information is accessed directly from the servers their stored in (data at rest), and one where information is collected while in transit (data in transit).
This distinction resonated with me, simply because I read about this a couple of months back when another wanted man name Kim Schmitz was making the news instead of one Edward Snowden.
