The Apple vs. FBI story has evolved so much in the past weeks, I thought I needed to write a separate post just on the updates. Admittedly, the story is far more complex and nuanced that I initially presumed, and everyone wants to be part of the conversation.
On one side, we have the silicon valley tech geeks, who seem to be unanimously in the corner of Tim Cook and Apple, while on the other we have the Washington D.C policy makers, who are equally supportive of James Comey and the FBI whom he directs.
But to understand this issue from a fair and balanced perspective, we need to frame the correct question, not just what the issue about, but who is the issue really focused on.
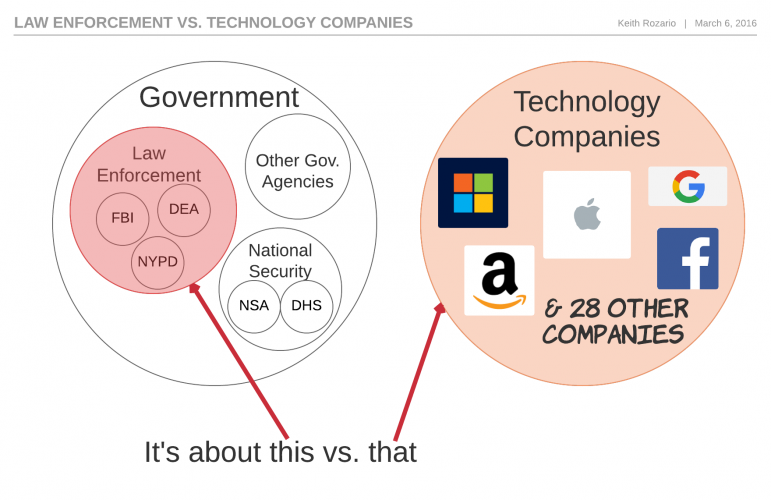
This isn't just about the FBI or Apple
Framing this as the
FBI vs. Apple or
The Government vs. Apple is wrong. This is
Law Enforcement vs. Tech Companies.The FBI is just a part of the The Government, specifically the part tasked with investigating federal crimes.James Comey, FBI director, is genuinely trying to do his job when he uses the All Writs Act to compel Apple to create a version of iOS that would allow them to brute-force the PIN code.
But there are other parts of The Government, like the NSA, who have the wholly different task of national security. To them, if a smartphone, is genuinely secured from FBI, then it’s secured from Russian Cybercriminals and Chinese State Sponsored actors too (probably!).
And because so much data are on smartphones, including the smartphones of federal government employees, the national security interest of America is better protected by having phones that are completely unbreakable, rather than ones the provide exceptional access to law-enforcement. Exceptional being defined as, no one has access except for law enforcement, and perhaps TSA agents, maybe border patrol and coast guard–you can see how slippery a slope ’exceptional’ can be. Oh and by the way, exceptional doesn’t exist in end-to-end encryption.
Former NSA director, Michael Hayden, has openly said “I disagree with Jim Comey. I actually think end-to-end encryption is good for America”. So it appears the NSA has an interest of national security that competes with the FBIs interest of investigating crimes.
The Government isn’t a single entity with just one interest, rather it is a collection of agencies with sometimes competing objectives, even though they all ultimately serve their citizens. Experts believe the NSA has the capability to crack the iPhone encryption easily, but are refusing to indulge the FBI, because–well it’s hard to guess why the NSA don’t like the FBI.
testimony to House Judiciary Committee. Both methods involved complicated forensics tools, but would cost a few hundred thousand dollars (cheap!) , and wouldn’t require Apple to write a weakened version of iOS. If the goverment can get into the phone for $100,000 , that would mean it couldn’t compel Apple under the All Writs Act (AWA).
Remember, the FBI buy their spyware from the lowlifes at hacking team, which means they’re about as competent as the MACC and Malaysian PMO, but if Comey and Co. can afford $775,000 on shit from Hacking Team, I’m guessing $100,000 for a proper computer forensics expert isn’t a problem.
But maybe there’s an ulterior motive here, at the very recently concluded Brooklyn iPhone case, Magistrate Judge Orenstein noted that necessity was a pre-requisite for any request made under AWA, and if the FBI have an alternative for a reasonable price, then Apple’s support was not necessary, and hence outside the ambit of the AWA. So maybe the NSA isn’t providing the support to necessitate the NSA.
An this isn’t singularly about the FBI either. The New York A-G is waiting for this case to set precedent before he makes request for the 175 iPhones he’s hoping to unlock for cases that aren’t related to terrorism or ISIS. You can bet he’s not the only A-G waiting for the outcome, and it’s highly unlikely for the Judge to make her ruling so specific that nobody except the FBI could use it as precedent.
But it’s also not just about Apple. The legal precedent set by this case would apply not just to every other iPhone, but possibly every other smartphone, laptop, car or anything else we could squeeze into the definition of a computer. This is about more than Apple, and that’s why the tech companies are lining up in support of Mr. Cook, 32 such companies the last I checked.
But now that we’ve framed the ‘who’ , let’s frame the ‘what’.