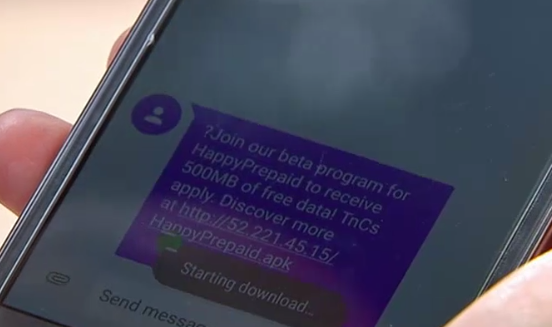
Channel News Asia posted last week that hackers could steal your info by just knowing your phone number.
Woah!! Must be some uber NSA stuff right–but no, it was a couple of guys with Metasploit and they required a LOT more than ‘just’ the phone number.
The post was an add-on to a current affairs show called Talking Point, that aired an episode last week about cybersecurity, which (like most mainstream media reporting) had more than a few errors I’d like to address.
Problem 1: Cost of cybercrime — but no context
The show starts off, by highlighting that Cybercrime cost Singaporeans S$1.25bln, which might be true, but lacks context, or rather had the context removed.
Because the very report that estimated the cost, also mentioned that society was willing to tolerate malicious activity that cost less than 2% of GDP, like Narcotics (0.9%) and even pilferage (1.5%). S$1.25bln is less than 0.3% of Singapore’s GDP, and is long way off the 2% threshold. Giving out big numbers without context gives readers the wrong impression.
So allow me to provide context on just how big that S$1.25bln is.
In 2010, Singapore’s retail sector lost S$222 mln to shrinkage, a term used to describe the losses attributed to employee theft, shoplifting, administrative error, and others. Had we split the cost of cybercrime across different industry based on their percentage of overall GDP, the total losses for cybercrime on the retail sector in 2015 would be $225 mln–almost identical to what the sector lost to shrinkage….7 years ago!
Cybercrime is a problem, but not one that is wildly out of proportion to the other issues society is facing.
Problem 2: Hacking with just a phone number
Channel News Asia headline their article with “Your phone number is all a hacker needs to track you, steal your info”, which isn’t true.
- The hackers sent an sms with a link, the victim willingly clicked on it, downloaded the app, opened the app, and then kept the app on the phone. This is clearly shown in the full episode, but somehow was redacted from their 2-minute clip.
- The host admits the sms was suspicious and clicked it anyway, in fact he even guessed it was from the hackers. Anytime you see a link with a odd IP address–you probably shouldn’t click it.
- I saw a meterpreter shell–which suggest that the hackers injected a payload into a standard apk file, and sent it to the victim to download.
- Which requires that the victim intentionally set his phone to allow unauthorized sources.
- This attack wouldn’t work on iPhone, blackbox place iPhone penetration in the island-nation at 73% (not a typo!) which means the attack wouldn’t work on most phones in Singapore.
- This attack, probably won’t work on a current Android phone with side-loading disabled either.
So, the attackers need your phone number, they need you to click a link, download a file, open the file, keep the program running and you have to intentionally disable security features on your phone–oh, by the way, this doesn’t work on iPhones.
The hackers need a whole lot more than your phone number.
I want to make clear just why these headlines piss me off so much.
Normal people in society, have no idea how technology works. Headlines like these are irresponsible because the trigger the wrong reactions. A ‘normal’ reading this would most likely stop sharing their number with people–but phone numbers were designed to be shared with people. You may be able to request anonymization of your mobile number–but that doesn’t work when you’re sms-ing or using whatsapp (where 90% of conversations are taking place).
Instead, we should prompt people to not root their phones, not click on suspicious links and for the LOVE OF GOD, don’t download software onto your phones from outside the approved stores–DON’T!!
Problem 3: WiFi sniffing
 Then we move onto unsecured WiFi.
Then we move onto unsecured WiFi.
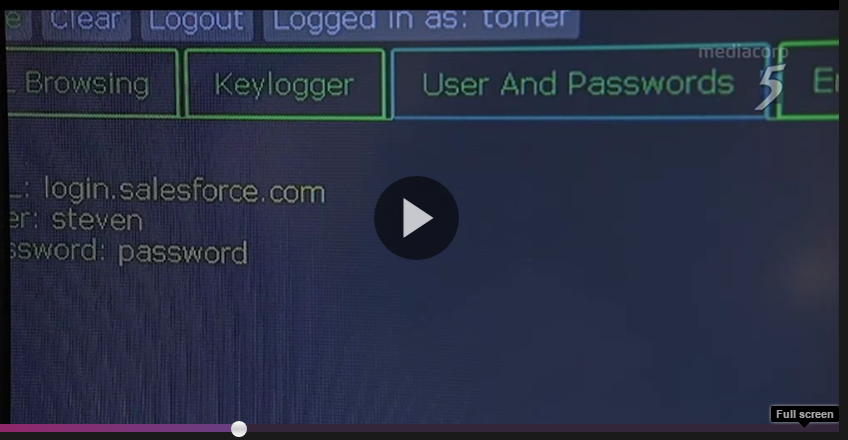
But the shows confuses unsecured WiFi with keyloggers. I’m not sure how connecting to a public WiFi installs a keylogger onto your device, but the segment starts with un-secured WiFi but quickly demo’s a keylogger on the phone.
Let’s get one thing clear–applications that have End-to-End encryption like Whatsapp and Signal are not susceptible to eavesdropping by anyone in the middle, whether that’s the government monitoring the undersea cables into a country, or a hacker on a Public hotspot. The segment suggest that somehow connecting to a public hotspots makes all your communication visible–it does NOT!
And the example they show is the url login.salesforce.com (screenshot). I checked, and this url doesn’t just have TLS enabled, it also has HSTS, which makes man-in-the-middle attacks near impossible. But I hear you say, what if the hacker compromised the phone, but that’s a different attack than an unsecured WiFi.
There was definitely somethings lost in translation between the geeks and the producers for this segment–if the keylogger was downloaded as part of the WiFi registration process that should have been made clear. I’ll let this pass because there’s too little content to make any judgement on it, other than it was way too brief.
In any case, using a VPN is probably better advice than downloading anti-virus software for your phone.
Problem 4: Ransomware advice
To be honest, they get this partially right. The solution they recommend for ransomware is backups.
What they left out, was that the backups need to be a separate location. Otherwise the ransomware will just infect your backups as well, like it did my uncle a few months back.
To properly protect yourself from ransomware–just get dropbox. Trust me…just do it.
Conclusion
So to conclude:
- Cybercrime is a problem, but financially it’s not that big of a deal–at least not yet.
- Hackers can’t hack your phone with ‘just’ your phone number–they just can’t.
- And the hackers that can, are probably not targeting you anyway
- And worrying about them is just not worth your time
- Avoid public WiFi like the plague of death
- But if you absolutely have to use one, use a VPN (I recommend PIA)
- Ransomware can cause you a lot of hurt, so to prevent it backup all your files using a cloud backup solution with versioning
- I suggest Dropbox
Don’t believe the mainstream media when it comes to ‘Cyber’ — refer to these sources instead:
For more focused blog-style content
For podcast (if that’s your thing):
And of course…keithrozario.com